Principles for the Sound Management of ...
After completing this reading you should be able to: Describe the three “lines... Read More
After completing this reading, you should be able to:
Ignored risks can pose serious challenges to a company. Therefore, the comprehensiveness of the risk identification exercise will determine how well-prepared an organization is for unfavorable events.
Risk identification is the first of the four crucial components of the risk management framework. The other three are risk assessment, risk mitigation, and risk monitoring.
A company’s board/executive sets the initial top-down criteria for the risk identification process. A company establishes departments, business units, and specific business processes from there. Besides, a company uses bottom-up risk identification method, in which different businesses and divisions assess their own operational risk.
A complete view of the top-down and bottom-up approach is referred to as “reconciliation.”
Top-down risk identification aims to isolate the most significant corporate risks that could compromise strategic goals. The approach employed in top-down risk identification is risk ranking and prioritization.
An analysis of the potential consequences of risks and projected effects on revenues should support the planning of top-down risk identification brainstorming sessions with senior risk owners.
The frequency of risk identification exercises at the executive level can be between two to four times annually, based on a business’ growth and development as well as the magnitude and rate of change of the new risks brought about by its operations.
When carefully carried out with participation from senior management, top-down risk identification is a useful tool for identifying the most important risks, boosting performance, and averting unpleasant surprises. The success of this strategy depends on establishing a strong control environment with the proper risk owners.
Bottom-up risk identification is the process carried out at the local company level, in a department, or at the level of a specific process.
The location inside the organization where risk identification takes place is the primary distinction between top-down and bottom-up risk identification methods. Senior leadership is involved in the top-down process of identifying risks, whereas staff members—including managers and non-managers—are involved in the bottom-up process.
Every financial institution has an inherent business risk vulnerability. Among others, risk vulnerabilities may stem from major sources of revenue, key customers, key persons, and regulators. Major risk exposures for a business typically include important third parties and large company projects. Should a failure occur in one of these activities, exposure increases the effects of risk.
Vulnerabilities are the weakest points in business operations. Resistance to risk management, overdue resolution of issues, and outdated processes enhance business operation vulnerabilities. A combination of vulnerabilities and potentially significant exposures can lead to huge losses or, perhaps, the demise of a company.
The key benefit of using a list of exposures and vulnerabilities as a brainstorming technique for risk identification is that it is business specific.
A risk wheel is a brainstorming tool used in risk identification workshops to promote originality and ideas.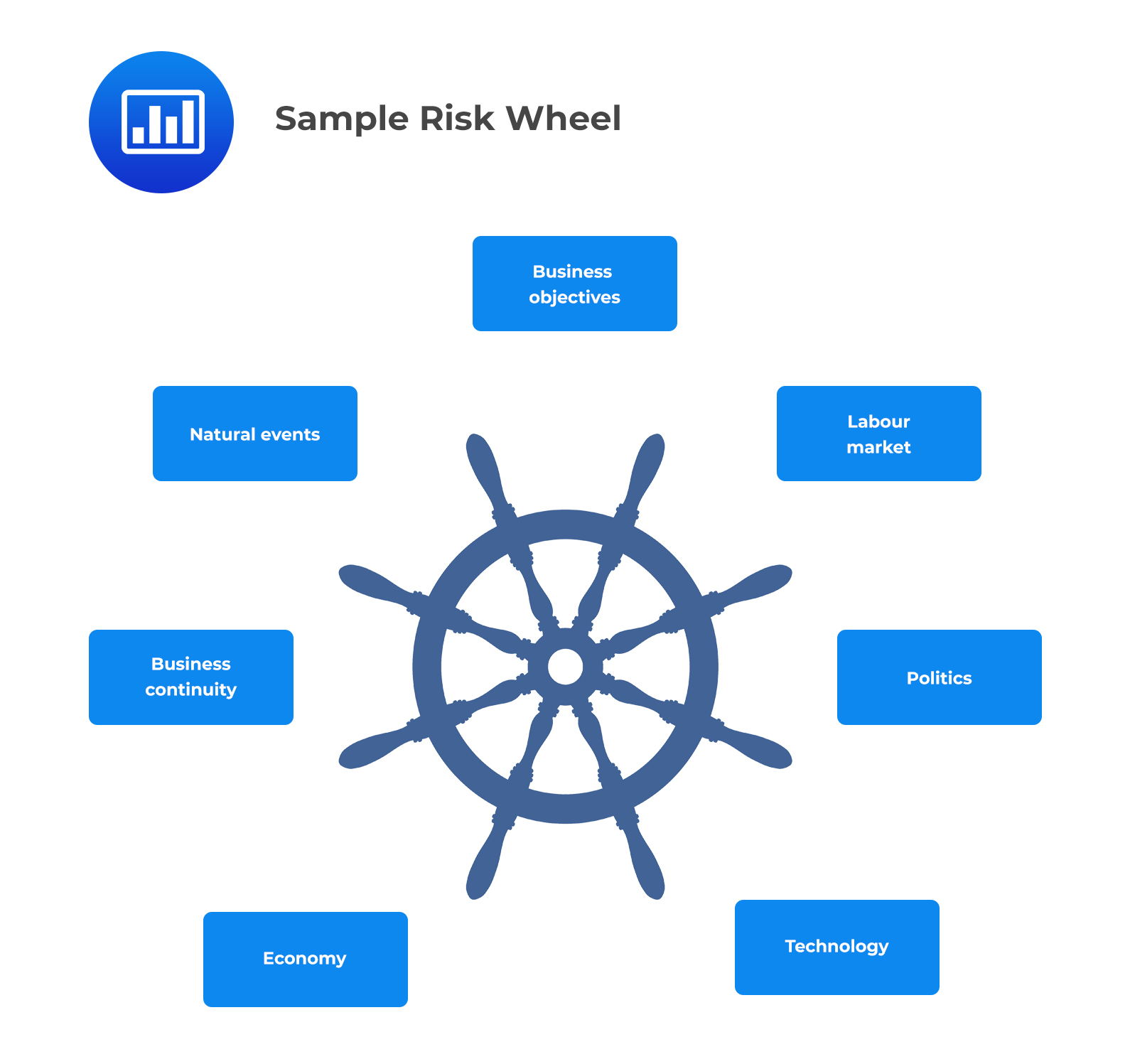
Natural disasters such as floods can have a negative effect on the supply chain and, in turn, affect business continuity. For instance, a power outage in a city where a fintech company’s data center is located can cause a business disruption for several days. Long-term business interruption negatively affects a business’ reputation.
When risk management prioritizes mitigating risks that can have adverse effects on other risks, it is far more effective in preventing a “domino effect.” The key to effective risk management is treating the root causes rather than the symptoms.
Horizon scanning is a popular technique for spotting new risks.
We can distinguish between known emerging risks that have already been observed in the past, such as employee well-being, and other nascent emerging risks that are only now starting to manifest on an organization’s risk radar.
Every year, several studies, polls, and publications, such as “The Global Risks Report” by the World Economic Forum, gather opinions from risk and business professionals on the risks they believe will dominate the agenda in the coming year. Even then, it is unlikely that all these risks will be relevant to a firm. For this reason, risk identification must be applicable to an organization’s unique circumstances.
The PESTLE analysis, an abbreviation for the many elements of an operational environment, is an organized method of scanning the horizon for risks.
In full, PESTLE stands for: P – Political, E – Economic, S – Social, T – Technological, L – Legal, E – Environmental
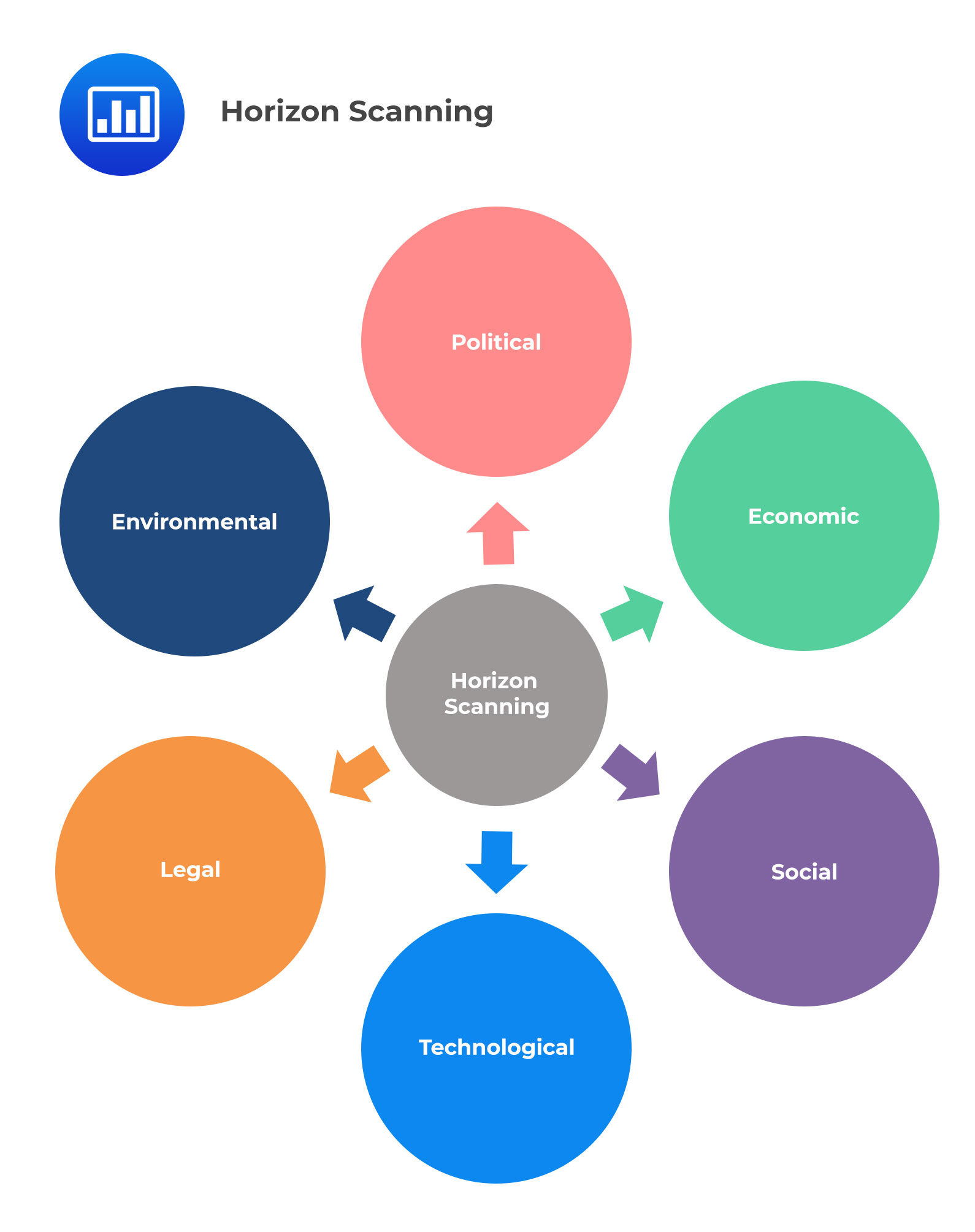
A company should concentrate its monitoring work on changes that affect its mission and approach, evolutions that could affect its long-term objectives, and new environmental changes that may affect business exposure or value drivers and threats that will be considered in scenario analysis and emergency preparation.
Some firms will use human expertise by creating “emerging risk committees” consisting of specialists from every area and region the firm operates in. Members of the committee gather regularly to review new developments and rumors of changes.
To detect operational risks, historical events at a company or among peers are a natural source of knowledge and inspiration.
Internal losses can be used to gauge how concentrated an organization’s operational risk is. Internal losses that keep happening could indicate a problem with the internal controls. Alternatively, such losses could represent the degree to which a company is exposed to operational risk. It is, therefore, imperative for a company to plan for these losses and factor them into the cost of financial products or services.
External losses, such as operational loss events, are typical data sources for identifying and assessing risks. A recommended approach is keeping an eye on all significant happenings that peers report and logically considering whether the same fate could befall your organization. If yes, your organization should assess its system of risk-mitigating procedures and controls to lessen the possibility of suffering losses.
Near misses are occurrences that might have led to a loss but did not as a result of good fortune or action outside an organization’s control. An example is sending funds to a wrong recipient but having the transaction reversed before you incur any loss. Near misses reveal flaws in the control system and show what might occur. The majority of businesses report near misses, which are then used as learning experiences to enhance safety culture and control the environment.
The process through which an organization or business line assesses the possibility and impact of its operational risks is known as a risk and control self-assessment (RCSA) exercise. RCSAs result in a self-evaluation of a business unit’s primary inherent risks, the key controls reducing those risks, and the effectiveness of those controls.
RCSAs are often used as risk identification exercises where business units come together in workshop meetings to discuss their concerns, and combine risk identification and assessment phases.
Selection of the appropriate participants significantly influences the quality of results in RCSA sessions. When conducting risk interviews, it is advisable to include two sorts of employees: those who have worked for a company for a long time and are familiar with its procedures and culture, as well as recent hires.
In mature firms, RCSA exercises are often conducted yearly and revised upon any major and pertinent changes to a firm’s risk environment.
Process mapping is a method of considering the risks associated with a set of activities. It involves outlining the tasks of a process step-by-step and asking what could go wrong in each phase. It can also be done by evaluating controls and determining the risks they are meant to address.
In order to use process mapping as a technique for risk identification, one must first identify the risk that each control mitigates and then consider what could go wrong at each stage of the process.
The first phase in scenario analysis, a crucial part of operational risk and capital evaluation, is scenario/stress-test identification. The scenarios that are evaluated in risk management often depict infrequent but extremely destructive catastrophes for companies, such as natural disasters and large cyberattacks.
The Basel Committee defines scenario analysis as “a process to find, assess, and quantify a range of possibilities, including low probability and high severity events, some of which could result in substantial operational risk losses.”
The Basel Committee recommends that banks should develop forward-looking business continuity plans (BCP) with scenario analyses linked to appropriate effect assessments and recovery procedures, such as identifying critical communication infrastructure or important clients.
Every scenario should go through a business impact analysis (BIA), also known as a business effect assessment, which weighs the financial, operational, legal, and reputational ramifications.
Recovery time objectives (RTO) and recovery point objectives (RPO) should be established as part of continuity procedures. Any third parties whom the real scenario would impact should be informed of the guidelines.
Consistency of approach and the reduction of behavioral biases are two major difficulties in scenario analysis. To meet regulatory requirements, a scenario analysis must produce quantitative and qualitative reproducible outcomes. The rationale for each scenario must be articulated. In addition, assumptions must be based on empirical evidence. Finally, the procedure for creating scenario analysis must be thoroughly recorded in order to prevent subjectivity and prejudice.
The preparation phase also entails assembling a “prepared pack” of documents that will be used to select and evaluate scenarios. These documents include internal loss data, external loss data, RCSA results, key risk indicator scores, audit issues and logbooks recording other issues, concentrated exposures, and any other relevant documents for risk and exposure assessment.
Senior managers from various corporate and business functions who have knowledge of the risks in their field should participate in scenario analysis workshops and brainstorming sessions. Though not a requirement, external experts may also be included in these sessions in order to mitigate biases such as myopia (the overestimation of recent events) and an overreliance on scenarios with external causes.
The generating phase, which comes first in a scenario analysis workshop, aims to create a lengthy list of scenarios. These scenarios are taken into consideration for inclusion on a short list of scenarios that will be presented for evaluation.
Scenario selection is an intermediary stage in which certain scenarios are combined, some removed, and others added to create a significant list to be adequately evaluated. To devote more time and energy to the review of larger and more pertinent situations, scenarios that appear to have little influence after a quick evaluation can be excluded at the selection phase.
To establish whether it has left out any important scenarios or risk factors, a firm may compare the scenarios it has created with a list of scenarios for the industry. This should be done after the scenario generation exercise to avoid the externally obtained scenarios biasing the scenario generation process.
According to the Basel Committee, operational risk is the risk of loss originating from inadequate or failing internal processes, people, systems, or external events.
Cause, event, and impact are the three components of risk, according to the International Organization for Standardization (ISO). Each risk is defined as a particular combination of a single cause, a single occurrence, and a single impact. Example: “Risk of cyberattacks (impact) due to phishing (risk) caused by delays in educating staff on how to prevent phishing (cause).”
The more precisely a risk is described, the simpler it is to connect it to its origins and effects, allowing for faster assessment, evaluation, and mitigation.
Technology-related risks are described as potential occurrences brought about by malfunctions such as system outages. Besides, manual processing is not a risk but a factor that raises the possibility of other risks. Risk assessment must consider the underlying causes of operational risk since processes that rely on technology may experience losses more frequently than manual processes.
Compliance with the regulations needs to be a priority. The risk is not in compliance per se but in breach of compliance. Regulation increases risks of losses such as compliance violations. Large penalties and fines may be imposed on a company that fails to follow regulations.
Risks should be defined explicitly and concretely in order to recognize and identify them. The more accurately a potential diverse event is described, the easier it will be to estimate the likelihood of its occurrence and to identify the appropriate mitigating steps. The best practice in the financial sector is to separate and categorize the many components of uncertainties, such as cause, risk, impact, and control.
Taxonomies are a structured manner of expressing causes, risks, impacts, and controls in progressively more detailed ways.
There are three levels in the official taxonomy of operational risks for banking institutions.
While level 3 is used as instances and illustrations, the Basel Committee only acknowledges the first two levels as regulatory categories.
$$\small{\begin{array}{l|l|l}\begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\textbf{Event-type}\\\textbf{Category}\\\textbf{(Level 1)}\end{array} & \begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\textbf{Categories}\\\textbf{(Level 2)}\end{array}& \begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\textbf{Activity Examples}\\\textbf{(Level 3)}\end{array} \\\hline
& \begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Unauthorized}\\\text{activities}\end{array} & \begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Transactions not reported (intentional)}\\\text{Transaction type unauthorized (w/monetary loss)}\\\text{Mismarking of position (intentional)}\end{array}\\\\\\\text{Internal fraud} & \text{Theft and fraud} & \begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Fraud/ credit fraud / worthless deposits}\\\text{Theft/ extortion / embezzlement}\\\text{Misappropriation of assets}\\\text{Malicious destruction of assets}\\\text{Forgery}\\\text{Check kiting}\\\text{Smuggling}\\\text{Account take-over / impersonation / etc.}\\\text{Tax non-compliance / evasion (wilful)}\\\text{Bribes / kickbacks}\\\text{Insider trading (not on firm’s account)}\end{array}\end{array}}$$
Many businesses employ a different operational risk taxonomy that is more tailored to their individual exposures and is dependent on the type, scope, and location of their operations.
An updated operational risk taxonomy was deemed necessary. Operational Risk Data Exchange (ORX) developed as a result of global financial sector trends such as technical breakthroughs, digitization, increase in cybercrime, and globalization of financial institutions with foreign operations. ORX is composed of the world’s largest banks and insurance companies.
The taxonomy offers some observable alterations but does not considerably depart from the Basel categories. Compared to Basel, it has 14 level 1 risk types, and some level 2 risks have been upgraded to level 1 due to their increased importance in the modern world.
A large proportion of businesses have level 2 risks that are better categorized as control failures, such as lack of training or resources.
Over the past ten years, the way risks are handled has evolved. While some businesses may classify cyber risk as category 1 risk, others may classify it as external fraud.
Arguably, lack of a universal reference is also to blame for the diversity of risk taxonomies used in practice across firms and fundamental disparities in business models.
Clarifying and categorizing operational risks, causes, impacts, and controls is critical in the development of an operational risk inventory and subsequent assessment of such risks. In addition, it makes risk mitigation easy.
Basel defines the taxonomy of causes as the possibility of financial loss occasioned by internal procedures, personnel, and systems that are insufficient or ineffective or by external developments. People, processes, systems, and external events are the natural level 1 causes of operational risk events.
The Basel Committee defines operational risk as the risk of loss, both directly and indirectly. Financial loss, reputational loss, regulatory non-compliance, and customer detriment are four common categories of the effects of operational risks.
The ORX has divided ‘PPSE’ level causes into people, processes, systems, and external events. These four categories are divided into competence, performance and ethics, systems design, performance and testing, process design, and governance failures at level 2. External events are further divided into political, regulatory, economic, and physical.
The impact categories list operational risks that a company is exposed to as a result of operational occurrences, including their direct, indirect, financial, and non-financial effects.
The taxonomy separates the impact effects such as disruption, reputation, regulatory enforcement, and types of stakeholders affected. The stakeholders could be customers, employees, or even third parties.
The four primary types of controls are preventative, corrective, detective, and directive controls.
The potential combinations of causes, control failures, and environmental change, categorized in taxonomies for an industry sector, can lead to a wide variety of risks that can have a number of effects. It is preferable for an organization to adopt a subset of these sector-wide taxonomies for its own risk inventory, often known as a risk universe. The inventory is a list of each of these risks, and it may be searched for, sorted, and used in many other ways to assist a business to understand the risks it faces.
The risk lists that businesses use most frequently are:
When it comes to maintaining and updating risk registers, it is normal to do so once every quarter or once a year for scenario identification and analysis, and once every three months for emerging risk assessment and horizon scanning.
Question
Which of the following statements best describes the role of the risk wheel in risk identification?
A. The risk wheel focuses exclusively on individual risks without considering their interconnections.
B. The risk wheel is used to proactively identify the root of a problem and understand the cascading effects of one risk on others.
C. The risk wheel is primarily a bottom-up approach to risk identification, focusing on granular operational details.
D. The risk wheel only helps in identifying external risks, such as market or credit risks.Solution
The correct answer is B.
The risk wheel is used to proactively identify the root of a problem and understand how different types of risks are interconnected. It offers a visual representation to understand the cascading effects of one risk on others, enabling risk managers to anticipate potential issues and their broader implications.
A is incorrect because the risk wheel, as described, does consider the interconnections between various risks. The example provided in the reading explains how a natural event (weather-related disaster) can lead to a problem in business continuity, which can then impact reputation.
C is incorrect because the risk wheel offers a holistic view of risks and their interconnections, making it a top-down approach. It doesn’t focus exclusively on the granular operational details of each risk but rather on the bigger picture of how risks are interconnected.
D is incorrect because the risk wheel encompasses a broad range of risks, both internal (like business continuity) and external. It does not solely focus on external risks such as market or credit risks.
Things to Remember
- A top-down approach starts with the overarching system or the broader perspective and then drills down to specific details. In the context of the risk wheel, this approach provides a holistic view of risks and their interconnected nature. For example, it understands how a broad event like a weather-related disaster can lead to specific risks such as business continuity issues and, subsequently, reputation risks.
- A bottom-up approach begins with specific, granular details and builds up to offer a comprehensive view. Contrary to the risk wheel’s methodology, this approach focuses on individual operational risks in isolation before understanding their collective impact. For instance, analyzing the operational intricacies of business continuity without initially considering its broader implications, like reputation risks, exemplifies a bottom-up strategy.