Repurchase Agreements and Financing
After completing this reading, you should be able to: Describe the mechanics of... Read More
After completing this reading, you should be able to:
Third-party risk management (TPRM) is the identification, assessment, mitigation, and monitoring of the risks associated with the usage of third parties, such as contractors, suppliers, service providers, and vendors. Third-party risk is also referred to as “outsourcing risk.”
To cut costs, financial firms frequently use third parties to provide services. They contract out a wide range of functions to specialized businesses with a competitive edge in certain systems, procedures, and expertise. Increased third-party risk exposure does, however, provide new challenges.
Risks fourth parties pose can also be managed as part of third-party risk management. These are suppliers of suppliers, subcontractors of service providers, or suppliers of the suppliers of the suppliers (fifth parties).
Service interruptions, poor service quality, fraud, unintentional or intentional information leaks, compliance violations, espionage, IP theft, and reputational harm are common third-party risks. Over time, the risk of “third party failure” has become more significant, constituting a level 1 category of operational risk for many institutions and the focus of specialized risk management techniques.
Financial companies are increasingly outsourcing core operations. These businesses usually have personnel who reside in countries other than the one where the contracting bank is situated. Along with country risk, outsourcing to a business in another legal system also carries compliance and legal risk.
Information security management, data privacy risks, and business continuity management all have a lot in common with TPRM. However, TPRM continues to be challenging for many firms.
In the past, regulators have established guidelines to assist banks in managing third-party risk. Regulators’ intervention notwithstanding, the complexity of the procedures and interactions between corporations has resulted in a flurry of newly suggested and proposed laws and guidance.
Shared Assessments, a US-based certification body that specializes in TRPM and provides third-party risk management specialists with professional certification, has proposed the TPRM life cycle shown below (CTPRP).
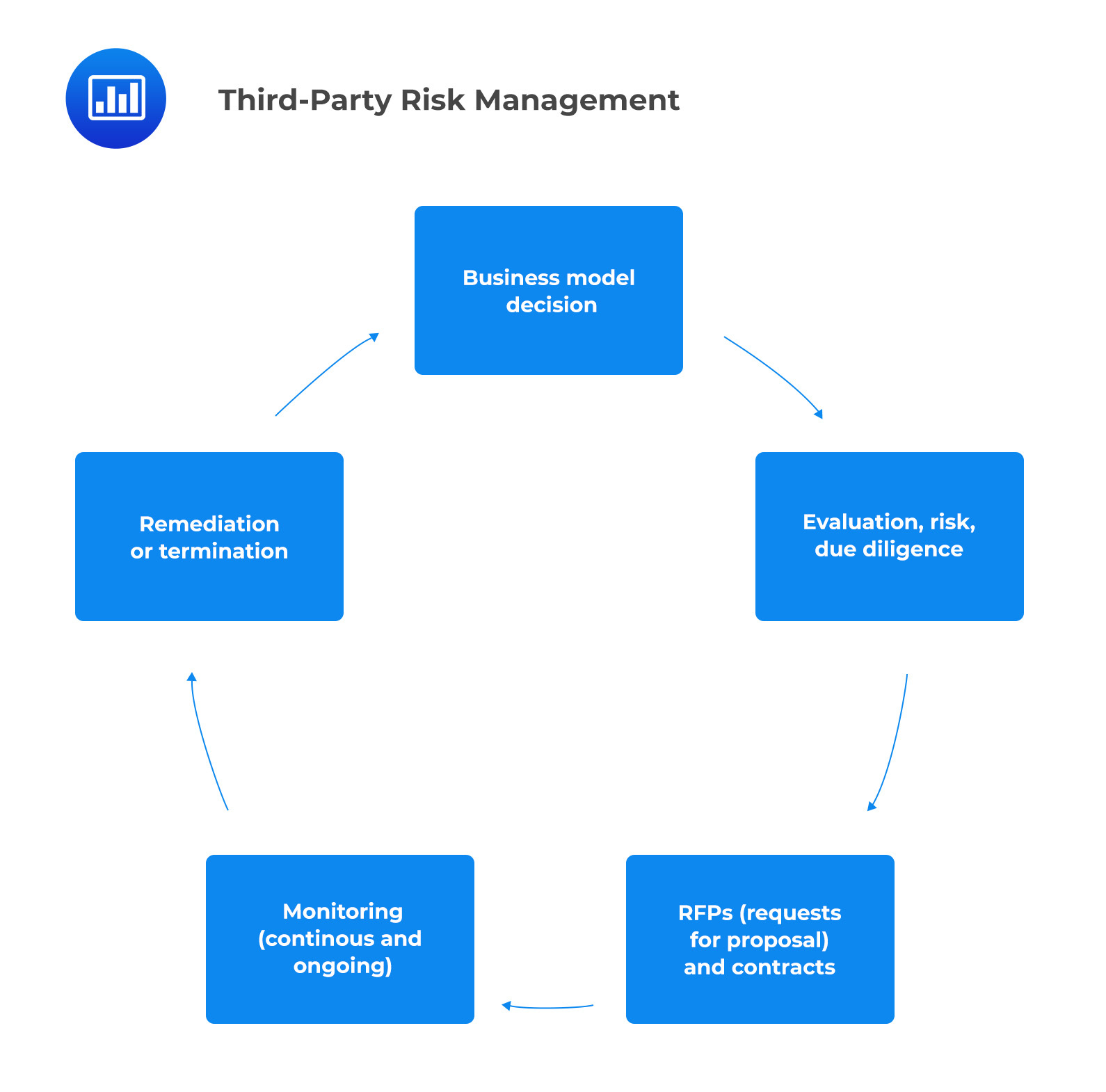 I. Business Model Decisions
I. Business Model DecisionsImportant strategic choices that relate to a firm’s risk appetite include the choice of whether to outsource or keep some tasks in-house and the choice of the quality and cost of the supplier.
A crucial element in TPRM is third-party evaluation and due diligence. Using a proportional approach to risk management is a good strategy. Due diligence and verifications necessary for an IT cloud provider responsible for hosting sensitive data are different from those required for an external consultant working for two days.
More businesses are using standard assessment questionnaires to streamline and standardize due diligence. The see businesses often use Shared Assessments’ SIG questionnaires.
In third-party management, contracts, service level agreements (SLAs), and contract management are the most disregarded essential areas of risk and control.
The contract’s terms should specify where, when, and what can and cannot be done. Besides, it should clarify what the players can and cannot do. Contracts (also known as Service Level Agreements, or SLAs), which determine the quality and timing of the supply of services, outline the obligations and expectations of both parties. One of the common causes of third-party relationship failure and operational risk increment is a lack of awareness or ambiguity in either party’s expectations. For this reason, it is advisable to clearly express these expectations in the contract, and an SLA, which should, wherever possible, include precise and quantifiable quality measures. Foreign-based service providers must also be aware of and abide by any local legislation that may be in force.
Contracts are only enforceable if both parties involved have signed them and only after all outstanding issues have been evaluated and resolved. Establishing the provisions of a periodic contract review to ensure compliance and a repair process to address contract shortfalls are both recommended.
A firm can manage third-party risk through contract terms. It’s best practice for a contract to set guidelines or restrictions on third-party vendors’ outsourcing. The standards for vendor outsourcing may largely be copies of the guidelines a company used for its own vendors. It is essential for companies to have the ability to audit their vendors. This is part of continuous monitoring.
Third-party relationship management (TPRM) includes monitoring service provision, quality SLAs, and compliance with the law and contract terms. The relationship agreement needs to be reviewed for continuation or modification. The shorter the reassessment and reviewing cycle, the more thoroughly the first four steps of the TPRRM life cycle are implemented. Determining reassessment trigger events is a good strategy and not simply set for end-of-contract or scheduled period assessments. Reassessment triggers can be particular occurrences such as data breaches, changes in business circumstances such as mergers, breaches of the contract, acts of God, or changes in the regulatory environment.
It is advantageous for businesses to have an exit strategy in case things do not go as planned.
Third-party partnerships end when the services are no longer provided; this is the usual reason for termination. Every contractual partnership should, however, have a grievance mechanism as well as an exit strategy or termination clause in case the relationship worsens beyond repair.
A third-party relationship might cease for a variety of reasons. It is noteworthy that in a third-party relationship, fairness is important. For this reason, both parties should prepare for a wind-down process that includes the transfer of intellectual property (IP), a plan to move to in-house services or another service provider, and to show that any sensitive data that the third-party vendor held has been transferred or destroyed.
A US bank called Capital One, which offers credit cards, auto loans, checking accounts, and savings accounts, disclosed that information on roughly 100 million Americans had been accessed unlawfully in 2019.
A former employee of Amazon Web Services, a provider of cloud computing services, was finally arrested by federal authorities and charged with hacking into the bank’s system and obtaining 140,000 social security numbers and 80,000 bank account data.
The attacker successfully accessed the files kept in an Amazon Web Services (AWS) database by taking advantage of a poorly configured web application firewall flaw. Encrypting the data to render it unusable for attackers would have been an appropriate remedy for this vulnerability. However, the bank did not encrypt its data.
In order to ensure that there were no additional instances of inappropriate setups in its environment, the bank fixed this issue. Even while the largest cloud service providers integrate excellent security into their solutions, risk management, monitoring, backups, and maintenance are an organization’s responsibility.
A US banking regulator penalized Capital One $80 million after finding that the bank had failed to set up efficient risk assessment procedures before moving important IT operations to the public cloud. The bank had a history of failing to recognize or correct its weak control environment.
US banking regulators fined Morgan Stanley $60 million for negligence in risk management and control of vendors during the decommissioning of two wealth management company data servers, as well as difficulties in decommissioning wide-area application service devices.
According to the regulator, the bank failed to sufficiently assess the risks of engaging third-party vendors, ineffectively assessed the risk of decommissioning its hardware, and failed to keep an appropriate inventory of client data on its devices.
The regulator claims that the bank neither chose the third-party contractors carefully nor appropriately assessed their performance. Upon discovering that some of the personal data from computers the bank had disposed of still remained on them, the regulator directed the bank to inform potentially impacted clients that their data might have been compromised. The bank gave the affected customers two years of free credit monitoring.
This instance demonstrates that while a firm may transfer some operational risks associated with an activity through outsourcing, it cannot transfer the responsibility for those risks.
Practice Question
Which of the following steps of the third-party risk management life cycle involves keeping track of service provision, quality SLAs, and compliance with the regulation?
- Remediation or termination.
- Business model decision.
- Evaluation and risk rating.
- Contract monitoring.
The correct answer is D.
Continuous monitoring involves keeping track of service provision, quality SLAs, and compliance with regulations as well as with the terms of the contract. It also involves setting trigger events for reassessment, not just at the end-of-contract.
A is incorrect. Remediation or termination involves having a grievance procedure as well as an exit strategy or termination clause if the relationship deteriorates beyond repair.
B is incorrect. The Business model decision step involves making the decision to either outsource some activities or keep them in-house. Besides, it involves consideration of a service provider’s quality and price. These are important strategic decisions that also relate to a firm’s risk appetite.
C is incorrect. Evaluation, risk rating, and due diligence involve sound due diligence and verification of third-party service providers. Proportionality of approach is a good risk management practice where there is need for extensive due diligence for third parties that will have access to sensitive information compared to those that will not.
Things to Remember
- Contract monitoring serves as a continuous oversight mechanism in the third-party risk management life cycle.
- It emphasizes tracking service provision, ensuring that the services delivered align with what’s agreed upon.
- Quality SLAs (Service Level Agreements) are key components in these contracts, setting clear standards and expectations for the third-party service provider’s performance.
- Monitoring also involves ensuring strict compliance with regulations and other stipulated terms within the contract.
- Effective contract monitoring can preemptively identify and address issues, reducing the potential for contractual disputes and misalignments.