Operational Resilience: Impact Toleran ...
After completing this reading, you should be able to: Describe an impact tolerance;... Read More
After completing this reading, you should be able to:
According to the international standards of enterprise risk management ISO 31000, there are four ways to address risks, labeled as “the four Ts”: tolerate, treat, transfer, and terminate.
Tolerating risk entails accepting it and taking no proactive steps to reduce or manage it. This strategy is commonly used when the cost of addressing the risk is greater than the potential losses that would be incurred if it were to occur. In such cases, companies assess the probability of risk occurrence and the potential severity of its consequences, then decide whether tolerating it is the most appropriate strategy for their particular situation. Companies monitor these risks on continuously to ensure they remain within acceptable parameters and can respond quickly if needed.
Treating a risk involves implementing measures to reduce or otherwise control its impact. This may include better staff training, investing in new technologies or systems, introducing additional procedures and controls, or increasing oversight and governance structures. This approach is often seen as a more proactive way to manage operational risks since firms can identify potential hazards before they occur and mitigate them accordingly.
Transferring risks involves transferring responsibility for them from one party to another to limit exposure. This can be done through contractual arrangements such as insurance policies, hedging activities, outsourcing services, or joint ventures with other firms. Such strategies enable companies to spread the financial burden associated with possible losses due to operational failures over multiple parties, thus reducing their overall financial exposure.
Terminating a risk means eliminating it from a firm’s operations. This could involve ceasing certain business activities altogether or divesting from certain areas where specific risks cannot be managed effectively. Companies may also decide to exit unprofitable markets after assessing all potential risks associated with continuing operations there. Such strategies are usually taken when other options have been exhausted, and companies feel that their financial capabilities are not sufficient enough to adequately manage the existing risks sufficiently well.
Among the four ways (discussed above) to address risk, treatment is the most common risk response, which involves risk mitigation through various control plans. Controls can be of different classes. In this discussion, however, we will use the classification the Institute of Internal Auditors used, i.e., preventive, detective, corrective, and directive controls.
These controls reduce the likelihood of an incident occurring. These controls also address the causes of potential risk events before they occur. Examples of preventive controls include segregation of duties – different parties perform different functions in a firm, access controls, level of authorization, and process automation.
Detective controls aim to alert the firm if an incident occurs to accelerate its resolution and limit the impact of the incident on the firm or its stakeholders. Detective controls include smoke alarms, intrusion detectors, and intrusion detection systems in cybersecurity. Credit card notifications of potentially fraudulent transactions are an example of detective controls. Once a cause of an event is detected, detective controls become preventive.
Corrective controls are intended to mitigate the impact of adverse events on an institution. Corrective controls include IT system redundancies, data backups, continuity plans, and crisis communication strategies. Corrective controls do not affect the likelihood of a risk occurring, but they reduce its pain if it does. When you back up your computer’s data, you won’t prevent the computer from crashing, but you will reduce the pain if the computer crashes. The use of seatbelts and airbags are common car accident corrective controls.
Directive controls provide guidance on how employees should handle certain situations that may arise while they’re performing their duties at work. Directive controls can include written plans outlining proper security measures to take when using the company’s computers, formal codes of conduct that employees must adhere to when dealing with customers or suppliers, or protocols for ensuring compliance with government regulations.
A key (primary) control is a control that can sufficiently prevent risk on its own. Most of the examples in the above figure are key controls. Key controls can be corrective if it neutralizes the impact of adverse events on an institution (as discussed above). A non-key control, on the other hand, can not sufficiently mitigate risk on its own. Rather, it complements the key controls.
Controls can be either manual or automated in nature. Automation significantly increases the reliability of any given control, making the mitigation process much more effective. The following are examples of automated controls:
With the advancement in modern technology, banks no longer find it reliable or reasonable to rely on manual controls. However, control automation is prone to human errors, which can transform into technology and model risk. Examples of issues that may arise in automated systems are:
Automated data backup processes occur on a full server, leading to data overflow and the absence of a backup.
The control assessment is an essential component of residual risk assessment. The effectiveness of risk mitigation measures must be tested (using control testing) to evaluate residual exposures to operational risk.
Financial risk management is shifting its focus from solely assessing risks to controls and assessing controls. The effectiveness of controls is observable and quantifiable. Observing risks is difficult, but observing their effects is easier. Testing controls should evaluate whether controls are conceived correctly, applied consistently, and evaluated properly.
Creating an effective control design is key to reducing risk and defending against threats. Poorly designed controls, however, are a waste of resources and provide a false sense of security. This can create openings for potential vulnerabilities in the system or environment, which could be devastating if exploited. Furthermore, ineffective control designs may result in the implementation of inadequate countermeasures that fail to properly address risks. Consequently, organizations must focus on creating meaningful designs that provide reliable protection through adequate roles and responsibilities, appropriate policies and procedures as well as robust infrastructure and processes.
Weakly designed controls can be of the following types:
The design and implementation of appropriate controls are essential for effective risk reduction. By carefully assessing the risks a process is exposed to and organizing tasks in such a way as to minimize their potential impact, one can create a secure system without needing to add additional controls. However, adding wrongly designed or untested controls can have the opposite effect, increasing the vulnerability of the process. To ensure that risk-reducing measures are fully effective, it is important to examine their performance once they have been put into place. Testing gives firms an opportunity to verify that controls are being implemented correctly and functioning as intended.
We have four primary types of control testing, presented in their level of scrutiny. The greater the inherent risk, the more rigorous the control testing must be.
The following are the main types of control testing:
The following factors influence the effectiveness of control testing:
This method, also called safety by design, involves applying, at the design stage, the methods and structures that will reduce risk events. Prevention through design includes risk mitigation techniques such as checklists, communication protocols, standardization, and optimized work environments or systems design.
Identifying slips and mistakes is the first step in categorizing human error. The following are categories of human errors and their mitigation:
Lean Six Sigma is a methodology that seeks to improve operational performance in businesses, organizations, and other areas. It combines two popular methodologies: Lean and Six Sigma.
Lean is a management philosophy based on eliminating waste and maximizing efficiency. The goal of Lean is to eliminate non-value-adding activities, maximize flow and reduce the time between customer order and delivery. The focus is on reducing lead times, improving cycle times, and shortening throughput times. Lean techniques traditionally focus on eliminating eight kinds of “waste.” Waste refers to various process inefficiencies associated with the underutilization of resources, time lost, or unnecessary tasks. The different types of waste are captured in the mnemonic “downtime,” which stands for defects, over-production, waiting, non-used talent, transportation, inventory, motion, and extra processing.
Six Sigma focuses on customer satisfaction by achieving near-perfect quality output at every step of a process. It uses data-driven decision-making to identify defects in processes through the implementation of five phases: Define, Measure, Analyze, Improve, and Control (DMAIC). This approach leads to an improved product or service offering that meets customer needs with few defects or issues.
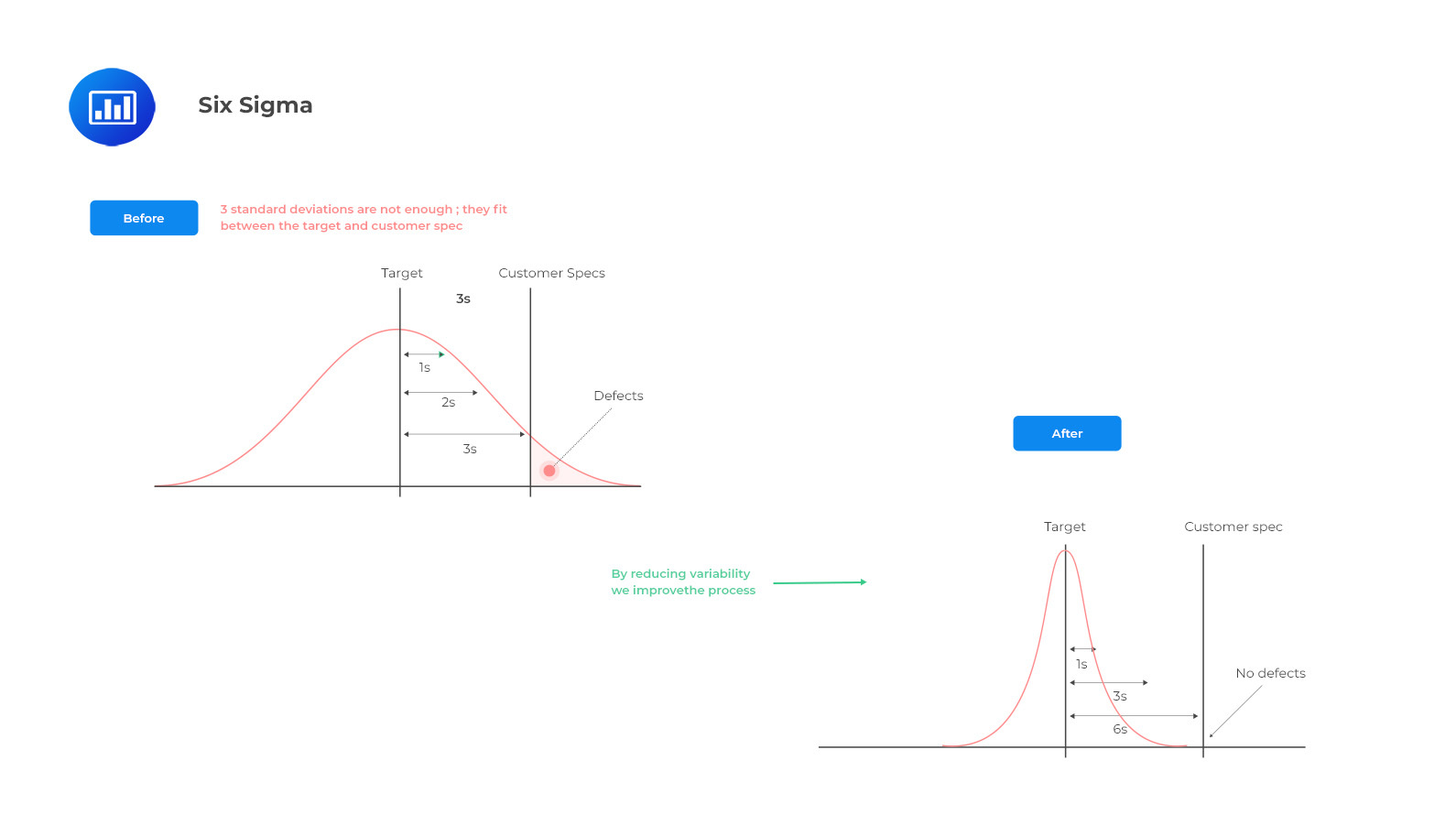
By combining these two methodologies into one system—Lean Six Sigma—businesses can achieve maximum efficiency with minimal defects throughout their operations. Lean Six Sigma helps companies identify waste in their systems by mapping out processes from start to finish and looking for opportunities to streamline them. It also uses data-driven decision-making to identify process issues so that they can be addressed quickly and effectively. Finally, it encourages continuous improvement by focusing on identifying small improvements over time rather than large changes all at once.
The following questions are key to addressing quality improvement:
It follows the plan, do, study, act (PDSA) cycle or “Dr. Deming cycle.”
The cycle is repeated to show product or service improvement clearly.
Businesses face significant operational risks when they embark on new projects, products, and initiatives that are unfamiliar to them. New Product Approval Process (NPAP) and New Initiative Risk Assessment Process (NIRAP) are two common risk-mitigation methods. Any plan or process that modifies or affects current business practices to achieve a business objective or solve a problem is considered a new initiative. New initiatives might include the following:
As a best practice, the owner of each new initiative should present a business case to show the allocation of resources. A good business case covers at least five topics, namely: objective, alternatives, expected benefits, commercial aspects, and risks
The degree of the operational risk function’s involvement depends on the level of risk, and mitigation required.
The project team itself manages typical project risks of time, budget, and delivery quality without involving the risk function. A usual project report on project risk and execution risk is then submitted to all stakeholders, including the risk function.
More mature firms would maintain a database of post-project assessments, debriefings, and lessons learned to either benefit from past stories or avoid repeating past mistakes. The risk function should ensure the effective use of past data and initiate the collection of lessons learned.
In addition to the traditional risks relating to time, budget, and scope, new initiatives can modify existing risks or create new ones by disrupting the state of business as usual. The ORM function should identify, assess, and mitigate all direct and indirect risks to support these new initiatives.
When projects are merged, the acquiring firm inherits the risks of the acquired assets. When a firm acquires assets, a portfolio, or the entire entity, it inherits all risks associated with those assets, necessitating more comprehensive risk management.
Credit risk can easily be assessed provided the data of collateral, obligors, and terms and conditions are available. Operational risk, on the other hand, is very difficult to be assessed since it is the risk that relates to the results of people, systems, and processes over time. Therefore, it may take time before the inherited operational risk is discovered. Banks should therefore be very keen to assess operational risks, especially when acquiring new assets. The ORM function can support these new initiatives by creating a risk profile to familiarize the management with potential operational risks related to these new business initiatives.
If a firm is acquired, it should be integrated to provide its own set of additional operational risks. The acquired firm should present customer and account platforms, payroll and management systems, and its communications with other companies. The ORM can help the firm identify these risks through risk identification workshops and work with the integrating teams to set mitigation measures to address potential risks related to a complex acquisition.
This section reviews key operational risk impact reduction measures, including contingency planning, resilience measurement, crisis management, and communication.
A contingency plan is simply a “Plan B” or an alternative action if the result of a future event does not go as expected. Contingency planning is part of business continuity management (BCM), disaster recovery plans (DRP), and corrective risk management. Contingency planning should clearly state who does what and when in case of an event. In broader terms, contingency planning involves providing alternatives in systems, people, and processes.
BCM and DRP are particularly relevant when considering operational resilience and the capacity to recover and adapt to incidents. BCM and DRP have been in place for decades.
Business continuity management is an ongoing process designed to keep the business running in the event of a crisis. It gives insight into where one’s business is vulnerable to disaster effects. In this case, it’s about identifying the critical areas and planning to maintain the business in the event of an incident.
A BCM structure is a manifestation of the business continuity plan (BCP), which ensures that the plan always works. The plan should be tested regularly for practicality and speed of implementation in case of an emergency. BCM governance is crucial, and as such, we should have a key owner responsible for designing actions and their execution, including communication with other parties.
The first step in BCM is to ensure senior-level commitment. The next step is to initiate the management process. After this, threats and risks should also be identified and linked to the firm’s key operational risks. Once these risks have been identified, actions should be taken to manage these risks as part of risk management. A business impact analysis is carried out to determine the terms of risk mitigation. Strategies and plans for mitigating these risks are developed and implemented accordingly. The plan is then tested and maintained.
The business continuity plan (BCP) will be activated in the event of disruptions. A firm should demonstrate three qualities when managing a crisis or major operational event:
In case of a crisis, firms should have at least two response teams:
There are four typical phases of a major operational risk event:
Risk can be transferred through external insurance or outsourcing.
Generally, external insurance reduces profit and loss volatility. The firm pays a regular premium in exchange for compensation in case of a risk event. External insurance policies for operational risk are suitable for operational risks that:
There is a trade-off decision between the insurance premium versus the volatility. Many firms will tend to self-insure small losses or absorb the volatility and only seek external insurance to cover losses from extreme operational events. Any large potential operational risk event, therefore, necessitates external insurance.
In external insurance, the risk is not necessarily fully transferred, as the amount of compensation depends on the premiums paid. In some cases, the firm may experience delays from the insurer, which may expose the firm to liquidity risks.
Outsourcing involves transferring the execution of a process to a third party. By doing so, some operational risk is also transferred in the process.
While FinTech banks usually manage their own technology but outsource credit risk management, traditional banks, on the other hand, handle credit decisions on their own but outsource some of their ICT operations.
However, outsourcing may result in third-party risk since the firm is exposed to the risk of failure of third-party controls. Furthermore, not all risks are transferable. The risk of accountability, for example, is not transferred through this process. Increasingly, outsourcing is perceived as a risk-sharing and not a risk-transfer method. Reputational damage is another risk that cannot be outsourced or transferred through insurance.
Operational risk controls and mitigation strategies can be implemented to protect a company’s reputation. Recall that reputational risk has been left out in the definition of operational risk. This is because reputational risk is not necessarily caused by operational risk. Both internal and external operational events can cause reputational risk.
One way to prevent reputational risk is to build and maintain customer confidence. The use of detective controls to identify operational failures and reduce their reputational effects are among the methods used to protect against them. Detective controls include monitoring customer complaints on social media and tracking refund requests or system downtimes.
Rewarding good behavior and best-rating performance can also help reduce potential financial and reputational losses. Firms should be careful when contracting third parties to avoid the wrong type of people with reputation issues.
Good reputational management comprises detective, preventive, and corrective measures. In case of an incident, corrective measures should follow the three Rs of crisis communication to stakeholders:
In addition to image and relationship building, stakeholder analysis contributes to an effective reputational management process. An organization’s stakeholders are not all equally important or affected by operational events. Stakeholder differentiation is essential when designing a specific remedy for a reputational risk event.
An interesting relationship exists between resilience and reputation: Stakeholder engagement and dialogue contribute to building the organization’s reputation capital. In times of crisis, this capital can serve as a cushion of goodwill to help reinforce the organization’s resilience to unanticipated shocks.
Robust crisis management and resilience will likely improve a firm’s reputation and vice versa.
Practice Question
A global financial institution is implementing a new risk management system and is considering various internal controls to enhance its risk mitigation efforts. The risk management team is tasked with identifying preventive and detective controls to be integrated into the system. Which of the following scenarios best exemplifies the use of both preventive and detective internal controls?
- The institution implements a segregation of duties policy, and managers provide guidance and manuals on how specific tasks should be performed.
- The institution conducts employee background checks and requires mandatory vacations for employees handling sensitive information.
- The institution enforces dual authorization for high-value transactions and uses a computerized system to monitor all transactions.
- The institution uses encryption for sensitive data and holds regular cybersecurity training sessions for all employees.
The correct answer is C.
Preventive internal controls are designed to prevent errors or fraud from occurring, while detective controls are designed to identify errors, irregularities, or fraud that have already occurred. Dual authorization for high-value transactions is a preventive control that reduces the risk of unauthorized transactions. The computerized system for detecting unusual transactions serves as a detective control, as it helps identify errors or fraud that may have already occurred.
A is incorrect. While segregation of duties is a preventive control measure, guidance and manuals serve as directive rather than detective controls.
B is incorrect. Both employee background checks and mandatory vacations for employees are preventive controls, as they aim to prevent potential fraud or errors from occurring.
D is incorrect. While encrypting sensitive data is a preventive control, cybersecurity training sessions can be seen as preventive/directive controls rather than detective controls.
Things to Remember
- The integration of varied internal controls enhances the resilience and robustness of a risk management system.
- Regularly updating and refining control measures is crucial to accommodate evolving threats and organizational changes.
- A well-rounded risk management approach often involves collaborating across departments to ensure holistic control implementation.
- Even the most stringent preventive measures can benefit from detective controls as a second line of defense.
- Internal control efficacy should be periodically assessed to identify potential gaps and areas of improvement.