Regression Diagnostics
After completing this reading, you should be able to: Explain how to test... Read More
After completing this reading, you should be able to:
An operational risk management framework is an approach to mitigating the risks associated with organizational operations. It involves identifying, assessing, monitoring, and controlling risks that could result in adverse outcomes that affect an organization’s ability to meet its goals and objectives. An operational risk management framework should include clear processes, policies, and procedures for identifying potential operational risks, assessing their severity, and developing strategies for reducing or eliminating them.
The Basel Committee defines operational risk as “the risk of loss resulting from inadequate or failed internal processes, people and systems, or external events.”
Operational risk encompasses a wide range of potential threats, including natural disasters, human mistakes, inadequate procedures or technologies, cyberattacks, financial losses due to fraud or theft, and reputational damage attributed to regulatory violations. To successfully manage these risks, organizations must have a comprehensive approach that incorporates all aspects of business operations. The focus of such an approach should range from employee roles and responsibilities to the use of technology and the development of data security protocols.
Many programs that manage risks in banks take effective management of operational risk as a fundamental element that is inherent in all banking products, systems, activities, and processes. Therefore, sound operational risk management reflects the board’s and senior management’s effectiveness in the administration of portfolio products, activities, processes, and systems.
Operational risk can also be referred to as non-financial risk. Some banks may have NFRM (Non-financial Risk Management) departments instead of ORM (Operational Risk Management) departments. This happens because factors that are not financial in nature often influence operational risk.
Enterprise Risk Management (ERM) is the term for the comprehensive management of all business risks.
In the financial sector, ERM offers a structure for managing an organization’s financial and non-financial risks from a firm-wide viewpoint.
Outside the financial industry, operational risks may account for the majority of a company’s risk exposure, resulting in no distinction between ERM and ORM.
The Basel Committee on Banking Supervision (BCBS) breaks down operational risk into seven major categories known as “Basel types level 1.”
The table below summarizes the seven level 1 categories of OpRisk according to the Basel committee.
$$\small{\begin{array}{l|l}
\textbf{Event Category} & \textbf{Definition} \\\hline
\begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Internal fraud}\end{array} & \begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Losses due to acts of a type intended to defraud,}\\\text{misappropriate property or circumvent regulations,}\\\text{the law or company policy, excluding diversity or }\\\begin{array}[c]{@{}l@{}}\text{discrimination events, which involve}\\\text{at least one internal party}\end{array} \end{array}\\\hline
\begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{External fraud}\end{array} & \begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Losses due to acts of a type intended to defraud,}\\\text{misappropriate property or circumvent the law,}\\\text{by a third party.}\end{array} \\ \hline\begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Employment}\\\text{practices and }\\\text{workspace safety}\end{array} & \begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Losses arising from acts inconsistent with employment,}\\\text{health or safety laws or agreements,}\\\text{from payment of personal injury claims or}\\\text{from diversity/discrimination events.}\end{array} \\\hline
\begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Clients,}\\\text{products, and }\\\text{business }\\\text{practices}\end{array} & \begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Losses arising from an unintentional or negligent failure}\\\text{to meet a professional obligation to specific clients}\\\text{(including fiduciary and suitability requirements), or}\\\text{from the nature or design of a product.}\end{array} \\ \hline
\begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Damage to }\\\text{physical assets}\end{array} & \begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Losses arising from loss or damage to physical assets}\\\text{from natural disaster or other events.}\end{array} \\ \hline
\begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Business disruption}\\\text{and system failures}\end{array} & \begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Losses arising from disruption of business or system failures.}\end{array} \\ \hline
\begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Execution, }\\\text{delivery and}\\\text{process management}\end{array} & \begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Losses from failed transaction processing or}\\\text{process management, from relations}\\\text{with trade counterparties and vendors.}\end{array} \end{array}}$$
Internal fraud includes any fraudulent activity a firm’s employees perpetrate. It is one of the less frequent types of OpRisk losses. It owes its rarity to the sophisticated internal control investments institutions have made over the years. However, cases of internal fraud still occur, and billions of dollars go down the drain.
$$\begin{array}{l|l}
\textbf{Event Category} & \textbf{Examples} \\ \hline
\text{Internal Fraud} &{\text{Transactions not reported (intentional);}\\ \text{transaction type unauthorized (w/monetary loss);}\\ \text{mismarking of position (intentional).}}\\\\ &{\text{Fraud/credit fraud/worthless deposits};\\ \text{theft/ extortion/embezzlement/robbery};\\ \text{misappropriation of assets},\\ \text{malicious destruction of assets;}\\ \text{forgery; check kiting;}\\\text{smuggling; account take-over/impersonation/ etc.};\\ \text{tax noncompliance/evasion (willful); bribes/kickbacks};\\ \text{insider trading (not on firm’s account)}}\end{array}$$
External fraud includes all forms of fraud third parties or outsiders perpetrate against a firm. In banking, good examples would be system hacking and cheque and credit card fraud. In recent years, external fraud has cost financial firms millions of dollars.
$$\begin{array}{l|l}
\textbf{Event Category} & \textbf{Examples} \\ \hline
\text{External Fraud} & {\text{Theft/robbery; forgery; check kiting}\\ \text{ Hacking damage; theft of information }\\ \text{(w/monetary loss) }}\end{array}$$
EPWS is more prominent in parts of the world where labor laws are either old-fashioned, or there is more of a culture of litigation against employers.
$$\begin{array}{l|l} \textbf{Event Category} & \textbf{Examples} \\ \hline \\
{\text{Employment Practices}\\ \text{and Workplace Safety}} & {\text{Compensation, benefit, termination issues;}\\\text{organized labor activity.} \\ \text{General liability (e.g., slip and fall.);}\\ \text{employee health and safety rules events;}\\ \text{workers compensation.} \\ \ \text{All discrimination types.}} \end{array}$$
This is one of the categories that have the highest numbers of loss events, particularly in the US. It encompasses losses, for example, from disputes with clients and counterparties, regulatory fines due to improper business practices, or wrongful advisory activities.
$$\begin{array}{l|l}
\textbf{Event Category} & \textbf{Examples} \\ \hline
{\text{Clients, products,}\\ \text{and business}\\\text{practices}}& {\text{Fiduciary breaches/guideline violations;}\\ \text{disclosure issues (e.g., KYC);}\\ \text{retail customer disclosure violations;}\\ \text{breach of privacy;}\\\text{misuse of confidential information.}\\ \text{Antitrust; improper trade practices;} \\ \text{market manipulation;}\\ \text{insider trading (on firm’s account);}\\ \text{unlicensed activity; money laundering.}\\ \text{Product defects (e.g., unauthorized);}\\ \text{model errors.}\\ \text{Failure to investigate clients as per guidelines,}\\ \text{exceeding client exposure limits.} \\ \text{Disputes over the performance of advisory activities}} \end{array}$$
The other operational risk involves physical asset damage. This can result from natural disasters or external human sources (e.g., terrorism and vandalism). Only a few firms actively incur losses from this type of risk because events in this category are usually either too small or incredibly large.
$$\begin{array}{l|l}
\textbf{Event Category}&\textbf{Examples}\\ \hline \\
\text{Damage to Physical Assets} & {\text{Natural disaster losses};\\
\text{human losses from external sources}\\ \text{(e.g., terrorism, vandalism)}.}
\end{array}$$
Events under the BDSF category can be quite difficult to spot. For example, a system crash almost always comes with financial costs, but these losses would most likely be classified as EDPM. To illustrate this, consider the derivative department of a large bank that experiences a crash at 9:00 am. The IT department does all it can, including turning to backup plans, all in vain. The system regains normalcy at 5:00 pm when money markets are already closed.
On checking the status of the transactions, the bank learns that it needs to fund an extra USD 10 billion on that day. Since the markets are already closed, the bank is forced to negotiate special conditions with its counterparties. Unfortunately, the rates at which the transactions are settled ultimately end up being higher than the daily average. Although a BDSF event – a system failure –occasioned this loss, it will most likely be categorized as part of the next category, Execution, Delivery, and Process Management (EDPM). Alternatively, it could be ignored altogether.
$$\begin{array}{l|l}
\textbf{Event Category} & \textbf{Examples}\\\hline
{\text{Business Disruption and}\\ \text{System Failures}} &{\text{ Hardware; software};\\ \text{telecommunications; utility outage/disruptions.}} \end{array}$$
These are losses from failed transaction processing. Alternatively, these losses could emanate from process management from relations with trade counterparties and vendors. Losses of this event type are quite frequent since human error, miscommunications, and so on, can occasion them. Particularly, these losses are common in an environment where banks have to process millions of transactions per day.
$$\begin{array}{l|l}
\textbf{Event Category} & \textbf{Examples} \\ \hline
{\text{Execution,}\\\text{Delivery}\\\text{and}\\\text{Process}\\\text{Management}} & \begin{array}{@{\labelitemi\hspace{\dimexpr\labelsep+0.5\tabcolsep}}l@{}}\text{Miscommunication; }\\\text{data entry, missed deadline or responsibility;}\\\text{accounting error/entity attribution error;}\\\text{delivery failure;}\\\text{Failed mandatory reporting obligation;}\\\text{inaccurate external report (loss incurred).}\\\text{Client permissions/disclaimers}\\\text{missing legal documents missing/incomplete.}\\\text{Unapproved access given to accounts;}\\\text{incorrect client records (loss incurred);}\\\text{negligent loss or damage of client assets}\\\text{Nonclient counterparty misperformance;}\\\text{misc. nonclient counterparty disputes.}\\\text{Outsourcing; vendor disputes.}\end{array} \end{array}$$
The Basel Committee defines operational risk as “the risk of loss resulting from inadequate or failed internal processes, people, and systems or from external events.” Operational risk includes legal risk but excludes strategic and reputational risks.
Many programs that manage risks in banks take effective management of operational risk as a fundamental element that is inherent in all banking products, systems, activities, and processes. Therefore, sound operational risk management reflects the board’s and senior management’s effectiveness in the administration of portfolio products, activities, processes, and systems.
Legal risk is related to the enforceability or breach of contracts, the applicability of laws and regulations, and the risk of financial loss in the event of mistakes or breaches. Compliance refers to submission to all the rules and regulations that are relevant to a certain activity as well as the law.
Banks face huge fines and expensive business restrictions that regulators impose as a result of breaching laws and regulations.
Reputational risk stems from damage to an organization’s reputation, public image, or brand due to the negative impacts of an operational event. It can arise from a variety of sources, including corporate mismanagement, product failure, safety issues, data breaches and cyber-attacks, employee misconduct or negligence, regulatory or governmental actions/investigations, and other unpredictable events. External actors, such as competitors, activists, and media outlets can also cause reputation risk.
Strategic risk can have a significant impact on the success of an organization. It encompasses risks associated with decisions related to a wide variety of areas, such as mergers and acquisitions, capital investments, entry into new markets or product lines, pricing strategies, and restructuring. Poor strategic decisions may lead to financial losses due to impaired asset values, higher costs, lost opportunities for revenue growth, reduced efficiency in operations and processes, or missed market opportunities. Unsuccessful implementation of a strategy, due to inadequate control procedures and failure to monitor objectives effectively, can also result in losses.
There are four main tasks that make up risk management frameworks:
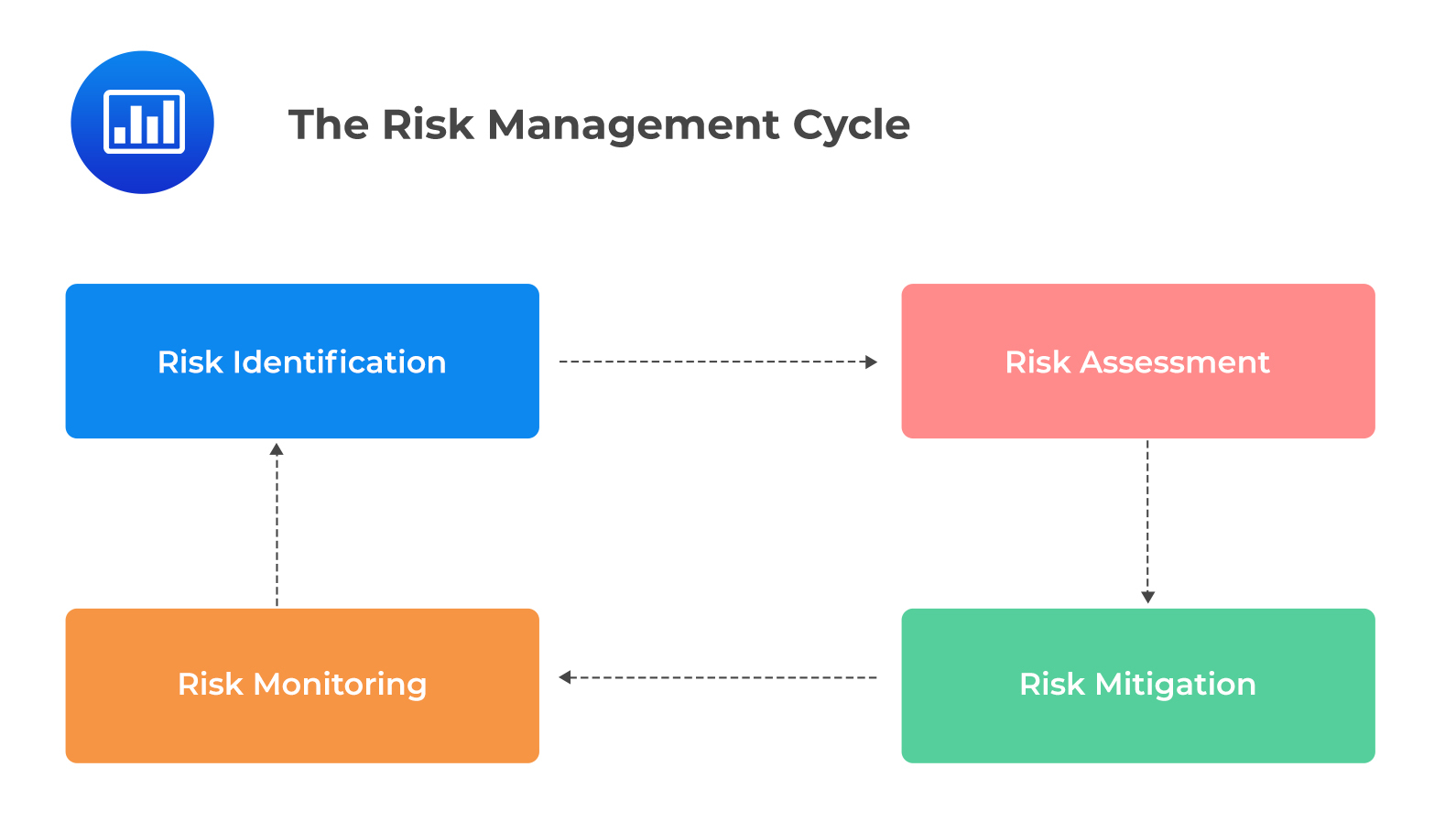 Risk identification is the process of identifying and analyzing potential risks that could affect an organization. This task involves determining which risks could have a material impact on the organization’s ability to meet its objectives and then gauging the likelihood of their occurrence. It also involves documenting any existing controls in place to mitigate those risks. Risk identification techniques include brainstorming, interviews with stakeholders, failure mode and effect analysis (FMEA), root cause analysis, examining industry trends, and other methods.
Risk identification is the process of identifying and analyzing potential risks that could affect an organization. This task involves determining which risks could have a material impact on the organization’s ability to meet its objectives and then gauging the likelihood of their occurrence. It also involves documenting any existing controls in place to mitigate those risks. Risk identification techniques include brainstorming, interviews with stakeholders, failure mode and effect analysis (FMEA), root cause analysis, examining industry trends, and other methods.
Risk assessment involves evaluating the probability of a risk occurring and its severity or impact if it does occur. This helps organizations prioritize their attention on the most significant risks so they can focus mitigation efforts where they are needed most. Different risk assessment approaches, such as qualitative or quantitative methods, may be used depending on the complexity of the subject matter.
Risk mitigation is implementing measures to reduce the likelihood or potential impact of each identified risk. Risk mitigation strategies include avoiding certain activities which pose a high risk, instituting control systems to monitor activities that could create unexpected events, transferring risks through insurance policies, and establishing quick response contingency plans.
Risk monitoring refers to the continuous tracking of risk exposure and how effective existing controls are at mitigating them. Organizations should regularly monitor identified risks to ensure that current controls are still valid and adjust them if necessary. Monitoring should also be conducted for changes in external factors that could cause an increase or decrease in risk levels over time. Among others, external factors include new regulations or market condition shifts.
There are five main characteristics of operational risk.
Operational risk encompasses an extremely broad range of risks, ranging from external fraud to cyber-attacks and data privacy breaches. Since each risk type can have different causes, consequences, and potential losses, it is important for firms to understand the risks they face in order to plan accordingly. For example, external fraud incidents can be caused by anything from stolen credit cards to malicious software infiltrations, whereas internal fraud incidents may include cash theft or rogue trading activities. It is also important for firms to consider the potential financial impact of each type of operational risk event. Risk financial impact varies greatly depending on the size and complexity of an organization.
Oftentimes the severity and frequency of operational risk events are largely dependent upon a firm’s ability and willingness to manage them effectively. Depending on the industry, certain risks, such as EDPM, might be more or less pronounced due to a company’s processes and systems. In addition, external events which are out of a company’s control can cause some risks, such as DPA. Therefore, it is critical for companies to continually assess their operational risk profile in order to best protect themselves against any future loss events.
This means that an organization may experience an occasional large loss even as it experiences numerous smaller losses on a regular basis. As such, traditional statistical models used to predict operational risk may not be effective due to their lack of capacity to accurately account for these extreme events. To address this issue, organizations should use alternative methods such as stress testing or scenario analysis to examine the potential impact of such events and plan accordingly.
A key feature of operational risk is the interconnectedness between different types of risks. For example, certain control weaknesses or human errors related to IT systems could lead to exposure across multiple departments and functional areas within an organization. Similarly, external economic, political, and environmental factors can also have a significant impact on operations due to their wide-reaching implications.
With industry developments, operational risks have taken on many different forms. These forms range from terrorist attacks and natural disasters to rogue trading and cyber-attacks. Operating environments are quickly changing, and so are operational risks.
Operational resilience is the ability of a business to proactively prepare for, respond to, and effectively manage disruptions. It is an important concept that allows a company to be better prepared and, thus, withstand unprecedented events and crises. The five main components of operational resilience are continuity of business services, important business services, impact tolerance levels, management of disruption, and lessons learned.
Continuity of business services refers to the capacity of a company to sustain essential operations and functions in the face of an unexpected event or crisis. This means that an organization should plan how it will sustain service delivery during such disruptive periods. In addition, a company should have mechanisms for monitoring performance and evaluating recovery from any service disruption.
Important business services are services that are fundamental to the success of an organization. Such services include both physical assets and intangible resources (such as skills). Organizations should be aware of all these important services so they can properly plan how they will manage them in case of failure or disruption.
Impact tolerance levels refer to the degree of adverse impact a business can tolerate before its operations are adversely disrupted. This is determined by assessing both internal capacities (such as available personnel) as well as external factors (such as government regulations). Organizations should be able to determine their own unique set of tolerable impacts in order to plan appropriately for disruptive events.
Management of disruption encompasses all activities aimed at minimizing any potential negative consequences occasioned by an unplanned event or crisis. This includes developing strategies that quickly restore normal operations while also ensuring minimal interruption in service delivery during such times. It also requires having strong communication plans in place so key stakeholders can be kept informed throughout the incident response process.
Lessons learned involve documenting any insights gained from managing a particular incident or crisis so as to avert similar occurrences in the future. Companies should create comprehensive reports outlining what went right and wrong in their response to previous disruptions. That way, they can apply these lessons when planning future responses and mitigation strategies.
The Federal Reserve (Fed) has issued its Sound Practices to Strengthen Operational Resilience. The regulation emphasizes the need for organizations to have a holistic enterprise management framework. This encompasses important business services, tolerance impact level, as well as consideration of operational resilience as one of the key outcomes of an effective ORMF.
Fed’s guideline stresses that organizations should have a comprehensive understanding of their critical operations and functions, including their people, processes, technology, and data. Thanks to this understanding, organizations can develop strategies to maintain operations despite potential disruptions. Organizations should consider the areas that may be at risk due to external factors such as cyber security threats or natural disasters. They should then moot plans to respond to the risks. Besides, they should identify key resources that are necessary for continued service delivery and secure them even in times of crisis.
There are seven BCBS Principles on Operational Resilience:
The three primary regulators that have policies for operational resilience are the UK, the US, and BCBS.
Practice Question
XYZ Bank is planning to improve its operational resilience framework. As a risk manager, you have been tasked with identifying the most critical aspects to prioritize in order to achieve greater operational resilience. Which of the following should be given the highest priority?
- Increasing cybersecurity defenses
- Enhancing backup and recovery procedures
- Identifying and protecting critical business services
- Implementing a more robust business continuity plan
The correct answer is C.
While all of the listed aspects are important for improving operational resilience, identifying and protecting critical business services (CBS) should be the highest priority. Operational resilience focuses on the ability of an organization to continue delivering critical operations and services despite disruptions, such as cyber-attacks, natural disasters, or technology failures.
Identifying and protecting critical business services involves understanding the most important functions and services that the bank provides, assessing their vulnerabilities and potential impact on the bank’s operations, and prioritizing their protection. By identifying and protecting CBS, the bank can ensure that the most crucial aspects of its operations can continue even during a disruption.
The other options, such as increasing cybersecurity defenses (A), enhancing backup and recovery procedures (B), and implementing a more robust business continuity plan (D), are all important components of an operational resilience framework. However, they are secondary priorities and are more effective when they support the protection and continuity of identified critical business services.
Things to Remember
- Operational resilience aims to ensure an organization’s ability to continue key operations and services despite various disruptions.
- Critical Business Services (CBS) are the vital functions and services a bank offers. Prioritizing CBS is paramount for achieving operational resilience.
- Understanding CBS includes assessing their vulnerabilities, understanding their importance, and safeguarding them against potential risks.
- Protection of CBS ensures that primary operations continue even during unforeseen events.
- While other resilience aspects like cybersecurity, backup, and business continuity are vital, they gain full significance when they back the protection of CBS.
Get Ahead on Your Study Prep This Cyber Monday! Save 35% on all CFA® and FRM® Unlimited Packages. Use code CYBERMONDAY at checkout. Offer ends Dec 1st.