Categories of Alternative Investments
With no true consensus as to any “official” categories of alternative investments, it’s... Read More
Distributed Ledger Technology (DLT) represents a technology with the potential to revolutionize financial services and record-keeping practices. Built upon a distributed ledger, a database that can be shared across an extensive network of entities, DLT networks are being explored to facilitate the creation, exchange, and tracking of ownership for financial assets on a peer-to-peer (P2P) basis.
The technology offers several potential advantages, such as heightened accuracy, transparency, and security in maintaining records, as well as faster asset ownership transfers and P2P interactions. However, it’s essential to acknowledge that DLT is not entirely immune to security risks, which may lead to privacy breaches and issues with data protection. Furthermore, the computational processes integral to DLT often demand significant energy resources to validate transaction activity.
For example, Bitcoin, a prevalent cryptocurrency, utilizes DLT to record all transactions. This approach establishes a transparent and secure means of transferring digital currency from one user to another without relying on a central authority like a traditional bank.
In a distributed ledger system, entries are logged, stored, and disseminated across a network of participants, ensuring that every involved entity possesses an identical copy of the digital database. This arrangement makes each iteration of the database a verified repository of all current and past transactions. Key components of a DLT network encompass a digital ledger, a consensus mechanism utilized to validate new entries, and a participant network.
The consensus mechanism stands as the method by which computer entities (or nodes) within the network come to an agreement on the shared status of the ledger. This process usually involves two phases: validating transactions and securing consensus among network participants to update the ledger. These mechanisms enable the generation of records that are typically considered immutable or unalterable while remaining transparent and accessible to network participants in nearly real-time.
Key aspects of DLT involve the use of cryptography, employing an algorithmic process to encrypt data, thus ensuring a high level of network security and integrity of the database. For instance, DLT utilizes cryptographic verification methods to confirm the identity of network participants and encrypt data.
DLT technology has the capability to support “smart contracts,” which are self-executing computer programs based on predefined terms and conditions agreed upon by contract parties. These smart contracts are useful in automatically executing contingent claims for derivatives and facilitating the instantaneous transfer of collateral in the event of default.
As an illustration, the Ethereum network incorporates smart contracts for automating contract execution. If an individual wishes to bet on the outcome of a football match, they can establish a smart contract on the Ethereum network. This contract will automatically disburse winnings to the victor once the match concludes, based on data obtained from a trusted source.
Blockchain is a type of distributed ledger where information is recorded sequentially within the blocks that are linked or chained together and secured by cryptographic methods.
The linking of blocks is regulated by the consensus protocol, which comprises a set of rules dictating how blocks can join the chain and establish an immutable record. These protocols are formulated to withstand potential malicious manipulation up to a specific level of security.
For instance, in order to add a new transaction to a network, the following key steps must be followed:
Step 1: Transaction occurs between the buyer and the seller
Step 2: A block containing the transaction information is formed and relayed to the network of computers (nodes).
Step 3: The computers (nodes) validated the transaction information and the involved parties
Step 4: After verification, the transaction is combined with other transactions to generate a new block of predetermined size of data for the ledger.
Step 5: The created block of data is linked using cryptography to the previous blocks or blocks containing the transaction data.
Step 6: The transaction is deemed complete, and the ledger has been updated.
It is noteworthy to state that each block has a group of transactions or entries and a secure link termed as a hash to the previous block. Moreover, new transactions are linked to the chain only after the validation through the consensus mechanism.
There are two main types of protocols in the blockchain technology. These protocols are distinguished based on their functionality and security level. The two main types of protocols are Proof of Work (PoW) and Proof of Stake (PoS).
The Proof of Work (PoW) serves as a consensus algorithm within blockchain networks, verifying transactions and adding new blocks to the chain. PoW determines which particular block to add using a computationally expensive lottery. Essentially, it involves a cryptographic problem that must be solved by power computers on a network (called miners) every time a transaction occurs.
Miners utilize robust computers and a substantial amount of energy to resolve complicated algorithmic puzzles, a necessary step in validating and securing transaction blocks on the blockchain. In doing so, they earn cryptocurrency rewards. Consequently, PoW requires significant energy consumption, hence making it costly for an individual third party to exploit historical data.
Proof of Work (PoW) consensus protocols, while effective, are vulnerable to a type of security threat known as the 51% attack. A ‘51% attack’ refers to an attack on a blockchain network by a group of miners controlling more than 50% of the network’s mining hash rate or computing power. In PoS, executing a ‘51% attack’ would require ownership of 51% of the cryptocurrency, which is financially disincentivizing, making PoS less susceptible to such attacks.
Within the blockchain network, participants collectively agree that the chain with the most blocks represents the authentic record of all previous transactions.
To successfully execute a 51% attack, a malicious actor must outperform the entire network’s computational power, effectively controlling over half of it. This immense level of computational control is the threshold at which the security of PoW protocols is compromised. Gathering such a significant portion of computational power is exceptionally challenging, especially on major blockchains like Bitcoin.
Despite its vulnerabilities, the PoW protocol remains the most widely adopted consensus mechanism for digital assets, largely due to the difficulty of executing such an attack.
In Proof of Stake (PoS) network participants known as validators pledge capital as a stake to affirm their commitment to validating transactions and proposing blocks. This staking acts as a signal to the network of a validator’s readiness to verify transaction accuracy and propose new blocks.
The process involves a majority of validators who have similarly staked digital assets, attesting to the legitimacy of each proposed block. Validators gain rewards (cryptocurrency or a token) both from proposing blocks and from attesting to the validity of blocks proposed by others engaged in the same staking process.
The security framework of PoS is based on a collective of stakers, utilizing their pledged stake to command the network’s computational power and thwart attempts by malicious entities to gain a controlling influence.
Distributed Ledger Technology (DLT) can be categorized into two types: permissionless and permissioned networks.
Permissionless networks are open to anyone who wants to make transactions and thus offer complete transparency, as all transactions on the blockchain are visible to every user. In these open Distributed Ledger Technology (DLT) systems, any participant can perform all network functions, encompassing a wide range of activities.
The primary advantage of permissionless networks lies in their independence from centralized authorities for transaction validation. Instead, transaction legitimacy is established through a consensus mechanism, eliminating the need for a single authoritative entity. This decentralization means there is no single point of failure, as all transactions are recorded on a unified distributed database, with every node holding a copy.
In a permissionless network, once a transaction is added to the blockchain, it becomes a part of a permanent and immutable record. In such networks, trust is not a prerequisite for transactions between parties.
Bitcoin, launched in 2009, is a prominent example of a permissionless network. It functions as the public ledger for all transactions involving its digital currency.
In permissioned networks, the participation of network members in certain activities can be regulated through a system of controls or permissions. These permissions determine the level of access each member has to the ledger.
For example, participants might be restricted from adding transactions, and regulators may only be allowed to view transactions or access only selected details of transactions.
Comparison between Permissionless and Permissioned Networks
$$\begin{array}{l|l|l}
& \textbf{Permissioned } & \textbf{Permissionless} \\
\hline
\textbf{Speed} & \text{Faster with limited member participation} & \text{Slower with more members to reach consensus} \\
\hline
\textbf{Cost} & \text{Cost-effective due to fewer member validators} & \text{Less cost-effective due to many member validators} \\
\hline
\textbf{Decentralization} & \text{Partially decentralized} & \text{Fully decentralized} \\
\hline
\textbf{Access} & \text{Membership limited} & \text{Unlimited membership} \\
\hline
\textbf{Governance} & \text{Determined by centralized authority} & \text{Decentralized; maintained by members} \\
\end{array}
$$
The adoption of Distributed Ledger Technology (DLT) has revolutionized the provision of financial services, streamlining processes such as tokenization, post-trade clearing, and compliance. Furthermore, DLT has been instrumental in the creation of digital assets like cryptocurrencies, enhancing the efficiency and delivery of financial services and investment management.
Digital assets are those that exist only on electronic records, with rights to use, buy, or sell. These digital assets enable almost instantaneous transactions between parties without requiring an intermediary.
Types of digital assets are summarized in the diagram below:
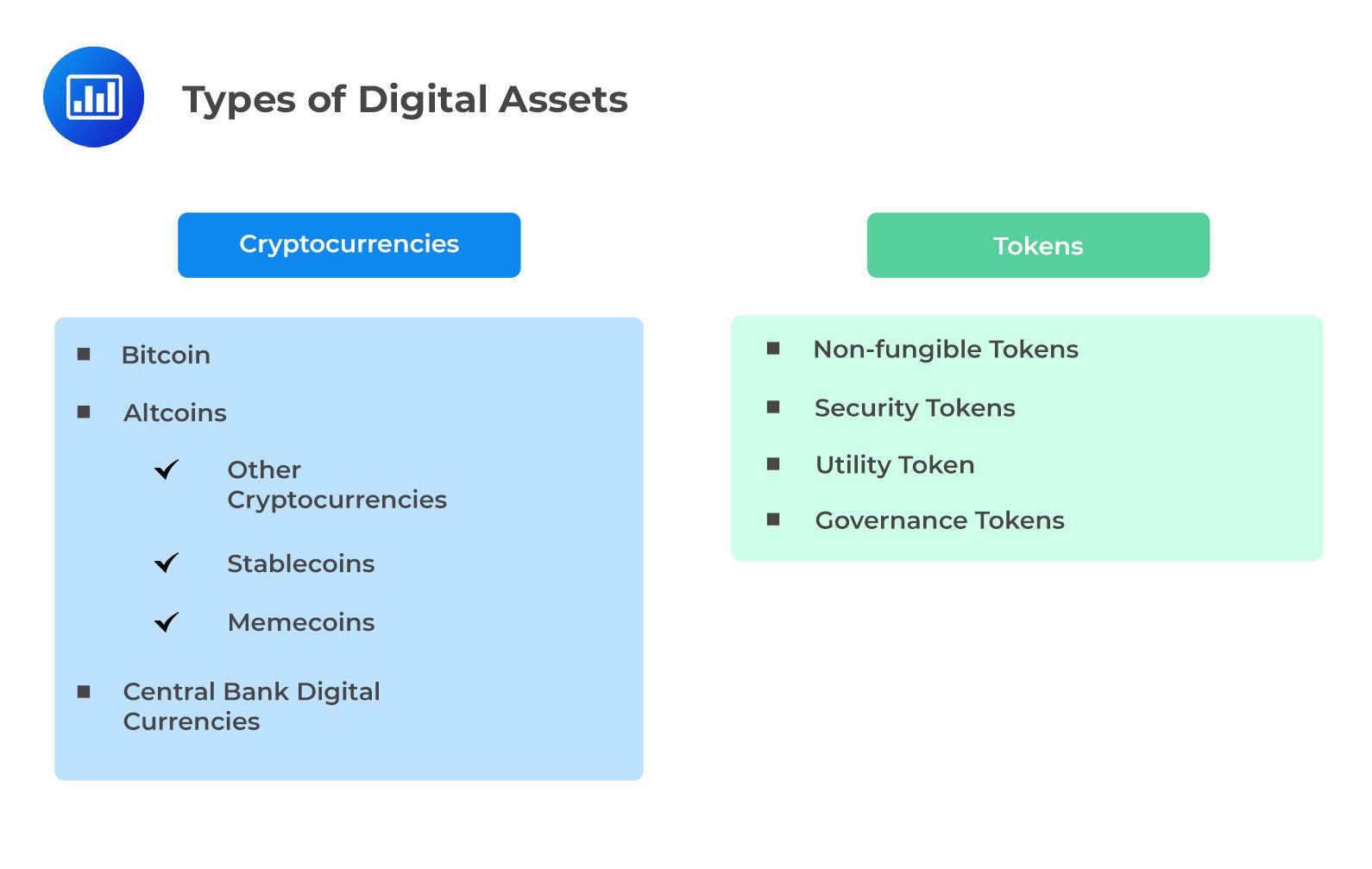
Cryptocurrencies are units that can be used to transfer or store value. They can serve as digital mediums of exchange that lack physical presence and are privately issued by individuals, companies, and other entities. They don’t rely on the support of a central bank or monetary authority. Typically, these currencies operate on open Distributed Ledger Technology (DLT) systems, utilizing decentralized distributed ledgers to record and authenticate digital currency transactions.
A number of cryptocurrencies implement self-imposed limitations on the overall amount of currency they can generate. While these limitations could potentially preserve their value, it’s crucial to recognize that many cryptocurrencies have encountered substantial price fluctuations.
Cryptocurrencies are not backed or regulated by the government. However, central banks worldwide are acknowledging the potential advantages and exploring potential applications for their unique cryptocurrency iterations, known as central bank digital currencies (CBDCs). These CBDCs generally represent a tokenized form of the fiat currency issued by the central bank (bank note or coin).
The transfer of ownership for tangible assets often involves substantial verification efforts with every change in ownership. Distributed Ledger Technology (DLT) has the potential to streamline this process through tokenization by establishing a unified digital ownership record that’s easily validated and transferred. This eliminates the necessity for extensive paperwork and legal formalities, thereby enhancing efficiency and transparency in the process.
Examples of tokens include:
Non-fungible tokens (NFTs):
NFTs constitute a distinct type of digital asset. They associate digital items with certificates of authenticity through blockchain technology. Each NFT corresponds to a unique authenticated object, effectively “stamping” assets and representing them within a virtual space.
Security Tokens:
Security tokens digitalize the ownership rights tied to publicly traded securities. These tokens’ custody can be maintained on a blockchain, streamlining post-trade processing, settlements, record-keeping, and custody procedures. This unified ledger approach eradicates the need for transaction validation and reconciliation, facilitating various transactions with enhanced ease and transparency.
For instance, initial coin offerings (ICOs) exemplify security tokens, where unregulated processes involve companies selling crypto-tokens to investors in exchange for funds or another agreed-upon cryptocurrency. In comparison to the regulated IPO market, ICOs may involve lower issuance costs and shorter capital-raising timeframes.
Conversely, utility tokens serve functions within a network, enabling payment for services and network fees. While security tokens might offer dividends, utility tokens solely compensate for activities conducted on the network.
Governance Tokens:
Governance tokens hold significance in permissionless networks by acting as voting tools that shape the operations of specific networks. For instance, within a decentralized finance (DeFi) platform, holders of governance tokens possess the authority to vote on modifications to the platform’s rules or parameters.
Question
In the context of permissionless networks, which of the following is most likely the primary function of governance tokens in a permissionless network?
- Provide a source of income for the token holders.
- Act as a medium of exchange for goods and services within the network.
- Serve as a voting mechanism to decide on the operation and changes in the network.
The correct answer is C.
The primary function of governance tokens in a permissionless network is to serve as a voting mechanism to decide on the operation and changes in the network. Governance tokens are a type of cryptocurrency that gives holders the right to vote on decisions that affect the protocol. They are a key component of decentralized finance (DeFi) platforms, which are built on blockchain technology and operate without a central authority.
In a permissionless network, anyone can join and participate, and decisions are made collectively by the network’s users. Governance tokens give holders the power to influence the direction of the platform, including decisions about technical upgrades, changes to the platform’s rules, and how funds are allocated. This democratic approach to decision-making is a defining feature of DeFi platforms and other decentralized networks, and it is made possible by the use of governance tokens.
A is incorrect. Although holding governance tokens can potentially provide a source of income if the value of the tokens increases, this is not their primary function. The main purpose of governance tokens is to give holders the right to vote on decisions that affect the network. Any financial gain from holding the tokens is secondary to this main function.
B is incorrect. While governance tokens can sometimes be used as a medium of exchange for goods and services within the network, this is not their primary function. The main purpose of governance tokens is to give holders the right to vote on decisions that affect the network, not to serve as a form of currency.
Get Ahead on Your Study Prep This Cyber Monday! Save 35% on all CFA® and FRM® Unlimited Packages. Use code CYBERMONDAY at checkout. Offer ends Dec 1st.